Attackers Continue to Target Java
Java’s security vulnerabilities can lead to viruses and malware on your Computer. Disabling Java in your browser may help keep your PC secure.
It’s no secret that Java has moved to the top of the target list for many attackers. It has all the ingredients they love: ubiquity, cross-platform support and, best of all, lots of vulnerabilities. Malware targeting Java flaws has become a major problem, and new statistics show that this epidemic is following much the same pattern as malware exploiting Microsoft vulnerabilities has for years.
Security researchers and software vendors have known![]() for a long time that attackers will wait for new patches to come out and then reverse engineer the fixes in order to find the specifics of the vulnerabilities. It’s a concern, especially for large vendors such as Microsoft, Adobe and Oracle whose software runs on hundreds of millions of machines and have regular, predictable patch cycles that attackers can depend on. This gives them a monthly or quarterly batch of fixes to sink their teeth into.
for a long time that attackers will wait for new patches to come out and then reverse engineer the fixes in order to find the specifics of the vulnerabilities. It’s a concern, especially for large vendors such as Microsoft, Adobe and Oracle whose software runs on hundreds of millions of machines and have regular, predictable patch cycles that attackers can depend on. This gives them a monthly or quarterly batch of fixes to sink their teeth into.
The attackers also know that many users don’t install new patches right away. Microsoft has succeeded in getting many of its customers to use automatic updates, especially in the enterprise. But there still are plenty of users, particularly consumers, who don’t take advantage of automatic updates, leaving them open to attacks. When it comes to Java, anecdotal evidence has supported the idea that even though there has been a steady stream of new vulnerabilities over the last few years, attackers have tended to focus most of their attention on older flaws for which patches already have been published.
Research from Microsoft shows that there has been a huge spike in malware targeting Java vulnerabilities since the third quarter of 2011, and much of the activity has centered on patched vulnerabilities in Java. Part of the reason for this phenomenon may be that attackers like vulnerabilities that are in multiple versions of Java, rather than just one specific version.
Jeong Wook Oh of Microsoft said,
“In Q3 and Q4 of 2012, two new vulnerabilities were found. But we didn’t observe any prevalence of Java malware abusing these newer vulnerabilities above malware abusing the older Java vulnerabilities. The reason behind this might be thatonly Java 7 installations were vulnerable to CVE-2012-4681 and CVE-2012-5076, whereas CVE-2012-0507 and CVE-2012-1723 also target Java 6. As there are still many users that use Java 6, the malware writers might have tried to target Java 6 installations by including older vulnerabilities in the exploit package. We can assume that, for this reason, they didn’t do away with the older vulnerabilities,”.
“So there were two kinds of Java vulnerabilities that appeared in 2012 overall: One is the category that applies to both multiple versions of Java including Java 6 and 7, and the other are the vulnerabilities that only applies to Java 7. So when new vulnerabilities that are only applicable to Java 7 are discovered, the attacker’s strategy was usually to combine it with older vulnerabilities that cover more versions of Java. In that way, they could achieve more coverage than just using a single exploit in one package.”
Microsoft looked specifically at four Java vulnerabilities from 2012 that malware targeted, only one of which was a zero day. The other three flaws already had patches available when the malware targeting them appeared. This is the same kind of pattern followed by malware that targets vulnerabilities in Microsoft products and Adobe applications. It, of course, just lends more support to the advice that security experts are always giving users: Install patches as soon as they’re available.
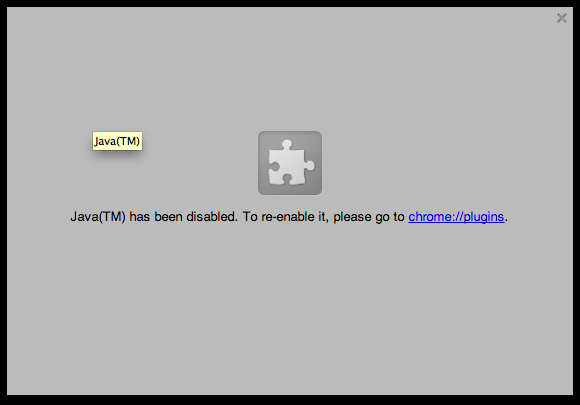 While many media reports will direct you to the Oracle website to promptly install the newest Java Updates and/or patches, there remains a far more secure option. Unless you’re one of the few Web users who regularly uses an important site that requires Java, take the advice of many security experts and just disable Java in your browser. Disabling the Java plug-in on your Web browser doesn’t require uninstalling it from your machine entirely, and it won’t prevent you from Java-based software outside of your Web browser. It just means that you’ll see a “Re-enable Java” prompt when you happen to visit one of the relatively few remaining websites that use Java applets. If you find you really need it for some sites, you can always disable it in your main browser but keep it enabled in a secondary browser that you use just for those sites.
While many media reports will direct you to the Oracle website to promptly install the newest Java Updates and/or patches, there remains a far more secure option. Unless you’re one of the few Web users who regularly uses an important site that requires Java, take the advice of many security experts and just disable Java in your browser. Disabling the Java plug-in on your Web browser doesn’t require uninstalling it from your machine entirely, and it won’t prevent you from Java-based software outside of your Web browser. It just means that you’ll see a “Re-enable Java” prompt when you happen to visit one of the relatively few remaining websites that use Java applets. If you find you really need it for some sites, you can always disable it in your main browser but keep it enabled in a secondary browser that you use just for those sites.
To disable Java:
– In Firefox, select “Tools” from the main menu, then “Add-ons,” then click the “Disable” button next to any Java plug-ins.
– In Safari, click “Safari” in the main menu bar, then “Preferences,” then select the “Security” tab and uncheck the button next to “Enable Java.”
– In Chrome, type or copy “Chrome://Plugins” into your browser’s address bar, then click the “Disable” button below any Java plug-ins. –
– In Internet Explorer, There is no way to completely disable Java specifically in IE, however, uninstalling the Java platform via Control Panel will remove it completely from your system
Original Article by Dennis Fisher View Original here
